In today’s interconnected world, the importance of cybersecurity cannot be overstated. As more and more of our daily activities, personal information, and critical business operations move online, the need to safeguard against cybersecurity threats has become paramount. FloraByte, a leading technology company specializing in cybersecurity, is committed to helping individuals and businesses stay protected in the digital landscape. In this blog post, we will explore some of the top cybersecurity threats that individuals and organizations face today and discuss effective strategies to defend against them.
The Ever-Evolving Landscape of Cybersecurity
Cybersecurity is a dynamic field, and threats continually evolve as technology advances. As such, it’s crucial to stay informed about the latest threats and trends. By understanding the risks, individuals and organizations can implement proactive measures to protect their data and systems. Here are some of the top cybersecurity threats to be aware of:
1. Phishing Attacks
Phishing remains one of the most prevalent cybersecurity threats. Attackers send deceptive emails, masquerading as legitimate entities, to trick individuals into revealing sensitive information or clicking on malicious links. Phishing emails often appear to be from trusted sources, such as banks, social media sites, or even colleagues.
Defensive Strategy: Educating users to recognize phishing attempts and implementing email filtering solutions can help mitigate this threat. Additionally, implementing two-factor authentication (2FA) adds an extra layer of security.
2. Ransomware
Ransomware attacks have surged in recent years. Malicious software encrypts a victim’s data, and the attacker demands a ransom for its release. Paying the ransom is risky and does not guarantee the safe return of your data.
Defensive Strategy: Regularly backing up data, maintaining up-to-date software, and employing strong security software can reduce the risk. Training employees to recognize suspicious links and email attachments is also crucial.
3. DDoS Attacks
Distributed Denial of Service (DDoS) attacks overwhelm a network or website with traffic, rendering it unavailable. These attacks can disrupt businesses and lead to financial losses.
Defensive Strategy: Employing a robust DDoS mitigation solution and having scalable infrastructure can help absorb and mitigate these attacks.
4. Insider Threats
Insider threats come from within an organization. Employees or contractors with access to sensitive information may misuse or abuse their privileges, intentionally or unintentionally.
Defensive Strategy: Implementing stringent access controls and monitoring user activities can help prevent insider threats. Regular security training and awareness programs are also essential.
5. Zero-Day Vulnerabilities
Zero-day vulnerabilities are unknown and unpatched security flaws that hackers exploit before developers can fix them. These vulnerabilities pose a significant threat as there are no available patches.
Defensive Strategy: Staying informed about the latest security updates and patches is crucial. Employing intrusion detection systems can help detect and respond to these threats.
6. IoT (Internet of Things) Vulnerabilities
The proliferation of IoT devices introduces new attack vectors. These devices often lack robust security features, making them vulnerable to exploitation.
Defensive Strategy: Segmenting IoT devices on separate networks, using strong passwords, and regularly updating firmware can help secure these devices.
7. Credential Stuffing Attacks
Credential stuffing attacks occur when attackers use compromised login credentials from one service to gain unauthorized access to other accounts. This threat is exacerbated by people using the same passwords across multiple services.
Defensive Strategy: Encouraging users to use unique, strong passwords and implementing multi-factor authentication (MFA) can deter credential stuffing.
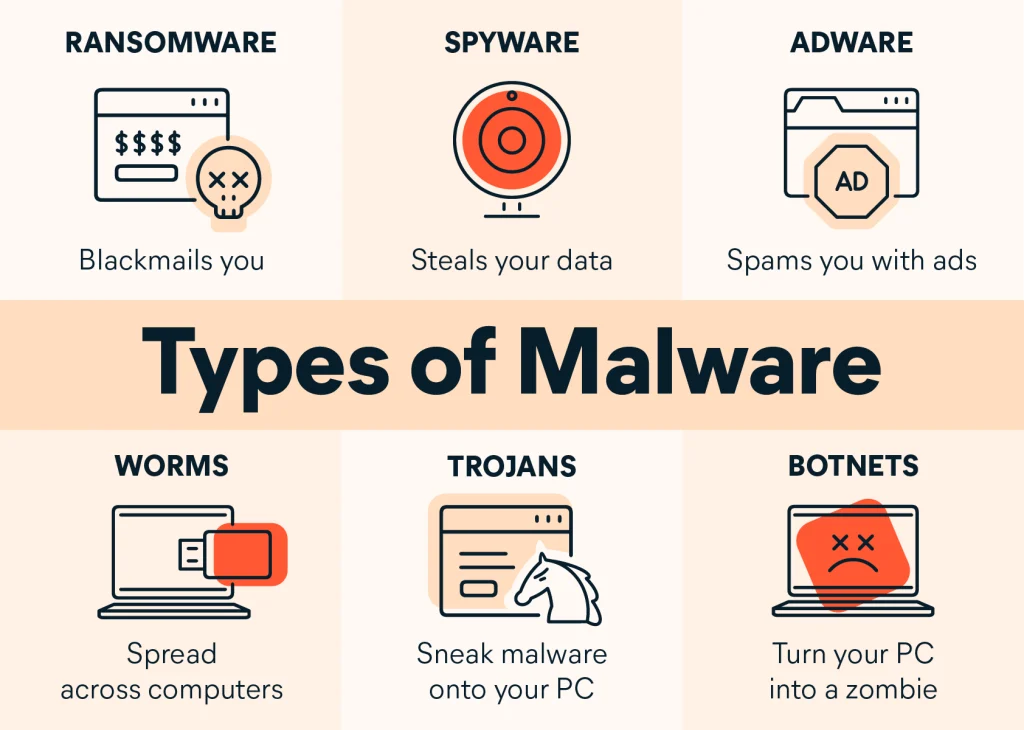
8. Malware
Malware, including viruses, worms, and Trojans, remains a persistent threat. These malicious software programs can infiltrate systems, steal data, or disrupt operations.
Defensive Strategy: Employing robust antivirus software, regularly updating systems, and educating users about the risks of downloading files from untrusted sources can help mitigate malware threats.
Conclusion
In the age of digital transformation, cybersecurity is a top priority for individuals and organizations alike. FloraByte is dedicated to providing cutting-edge solutions and expertise to address the growing challenges of cybersecurity. To protect against these top cybersecurity threats, it’s essential to stay informed, be proactive, and take the necessary steps to defend against potential attacks.
By implementing the defensive strategies discussed in this blog post, you can significantly enhance your cybersecurity posture. Remember, cybersecurity is an ongoing process, and staying vigilant is the key to safeguarding your digital assets and data in an ever-evolving threat landscape. If you need expert guidance or support in fortifying your cybersecurity defenses, don’t hesitate to reach out to FloraByte. Our team of cybersecurity experts is here to assist you in protecting what matters most.
